

Last updated on

WooCommerce recently issued a warning regarding an XSS vulnerability, coinciding with Wordfence’s alert concerning a critical vulnerability within a WooCommerce plugin called Dokan Pro. The Dokan Pro advisory highlighted a SQL Injection vulnerability, which enables unauthorized attackers to extract sensitive data from a website’s database.
The Dokan Pro plugin empowers users to convert their WooCommerce website into a multi-vendor marketplace akin to platforms like Amazon and Etsy. With over 50,000 installations, plugin versions up to and including 3.10.3 are susceptible to vulnerabilities.
As per WordFence, version 3.11.0 represents the fully patched and most secure iteration.
On WordPress.org, the lite version boasts over 50,000 current installations and a cumulative installation count exceeding 3 million. Presently, only 30.6% of installations have updated to the latest version, 3.11, indicating that approximately 69.4% of all Dokan Pro plugins may remain vulnerable.
The changelog serves as a crucial means for plugin users to understand the contents of an update. Typically, plugin and theme developers explicitly notify users when an update includes a patch for a vulnerability. However, according to Wordfence, the vulnerability affects versions up to and including version 3.10.3. Surprisingly, the changelog for version 3.10.4, released on April 25, 2024, which is supposed to address the vulnerability, does not indicate a patch. This omission suggests the possibility that the publishers of Dokan Pro and Dokan Lite chose not to alert potential hackers to the existence of this critical vulnerability.

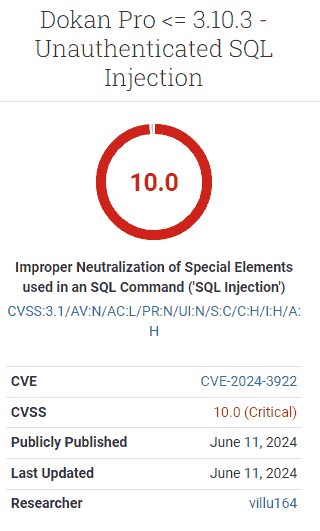
The Common Vulnerability Scoring System (CVSS) serves as an open standard for evaluating the severity of vulnerabilities by assigning a score. This score considers factors such as exploitability, impact, safety, and urgency, resulting in a total score ranging from 1 (least severe) to 10 (most severe).
In the case of the Dokan Pro plugin, it received a CVSS score of 10, indicating the highest level of severity. This suggests that all users of the plugin should promptly take action to address the vulnerability.
The discovery of an Unauthenticated SQL Injection vulnerability in Dokan Pro raises significant concerns. Unauthenticated vulnerabilities are particularly worrisome because attackers can exploit them without needing to obtain user credentials. Among types of vulnerabilities, unauthenticated ones represent the worst-case scenario.
In WordPress, an SQL Injection vulnerability occurs when a plugin or theme permits attackers to manipulate the website’s database. Since the database stores critical information such as passwords, login details, posts, themes, and plugin data, any vulnerability that enables unauthorized manipulation of the database poses a severe threat. Such vulnerabilities are highly concerning due to their potential for significant harm to the website’s integrity and security.
The Dokan Pro plugin for WordPress, in versions up to and including 3.10.3, contains a vulnerability susceptible to SQL Injection via the ‘code’ parameter. This vulnerability arises from inadequate escaping on user-supplied parameters and insufficient preparation on the existing SQL query. Consequently, unauthenticated attackers can exploit this flaw to append extra SQL queries to existing ones, potentially leading to the extraction of sensitive information from the database.
Dokan Pro plugin users are strongly advised to promptly update their sites. While it’s wise to test updates before going live, the severity of this vulnerability warrants expedited action.
WooCommerce has issued an advisory regarding a vulnerability impacting versions 8.8.0 and above. Rated at 5.4, it poses a medium-level threat and specifically affects users with the Order Attribute feature activated. Despite this, WooCommerce strongly urges users to update to the latest version, currently WooCommerce 8.9.3, at their earliest convenience.
The vulnerability affecting WooCommerce is known as Cross-Site Scripting (XSS), which relies on a user, such as a WooCommerce store admin, to interact with a malicious link.
According to WooCommerce:
“This vulnerability has the potential to enable cross-site scripting, a form of attack wherein a malicious actor manipulates a link to inject harmful content (typically JavaScript) onto a webpage. This could impact anyone who clicks on the link, including customers, merchants, or store admins.
We have not observed any instances of this vulnerability being exploited. Initially identified through Automattic’s proactive security research program in collaboration with HackerOne, our support teams have not received any reports of exploitation, and our engineering investigations have not uncovered any instances of exploitation.”
Adam J. Humphreys, a web developer and search marketing expert at Making 8, Inc., emphasizes the importance of web hosts taking a more proactive approach to patching critical vulnerabilities, even if it means potential conflicts with existing plugins or themes.
According to Adam:
“The underlying issue lies in the absence of automatic updates in WordPress, leaving sites vulnerable to exploitation. Most hosts neglect core updates, and plugin updates are often deferred until a core update occurs. Moreover, premium plugin updates, crucial for security, frequently require manual intervention.”
When asked about the possibility of push updates, where updates are forcibly applied to websites, Adam affirmed:
“Indeed, many hosts refrain from updates until a WordPress core update triggers them. Softaculous, a WordPress auto installer, confirmed this practice. Even WPEngine, boasting fully managed updates, doesn’t execute them frequently enough to promptly address plugin vulnerabilities. Given that WordPress powers half of all websites, this lack of ongoing management poses a significant security risk that needs urgent attention from WordPress developers.”
Original news from SearchEngineJournal